The data privacy landscape is rapidly evolving. There are big benefits to proactively addressing it and big consequences from ignoring it. Measurement is being limited and cookie consent is just the start. We need to ask for user consent before collecting data and establish a privacy first approach to marketing that benefits both brand and consumer.
Want a deep dive into privacy first marketing? Download our free guide to cookies and data privacy for marketers.
Building a Privacy First Marketing Technology Stack
To utilise technology effectively for consumer privacy protection and marketing performance enhancement, consider the following:
- Use tech to build more meaningful customer relationships
- Minimise the risk and maximise the rewards for compliance
- Build a best practice marketing technology stack
Use Tech to Build More Meaningful Customer Relationships
There is a competitive advantage in meeting your customers’ needs. Using technology with an understanding of customer rights leads to a competitive advantage. It allows us to meet the needs of our customers, all while adhering to privacy standards and maintaining a position of trust in the digital marketing landscape. By embracing these opportunities, we cultivate a relationship where respect for privacy drives competitive differentiation.
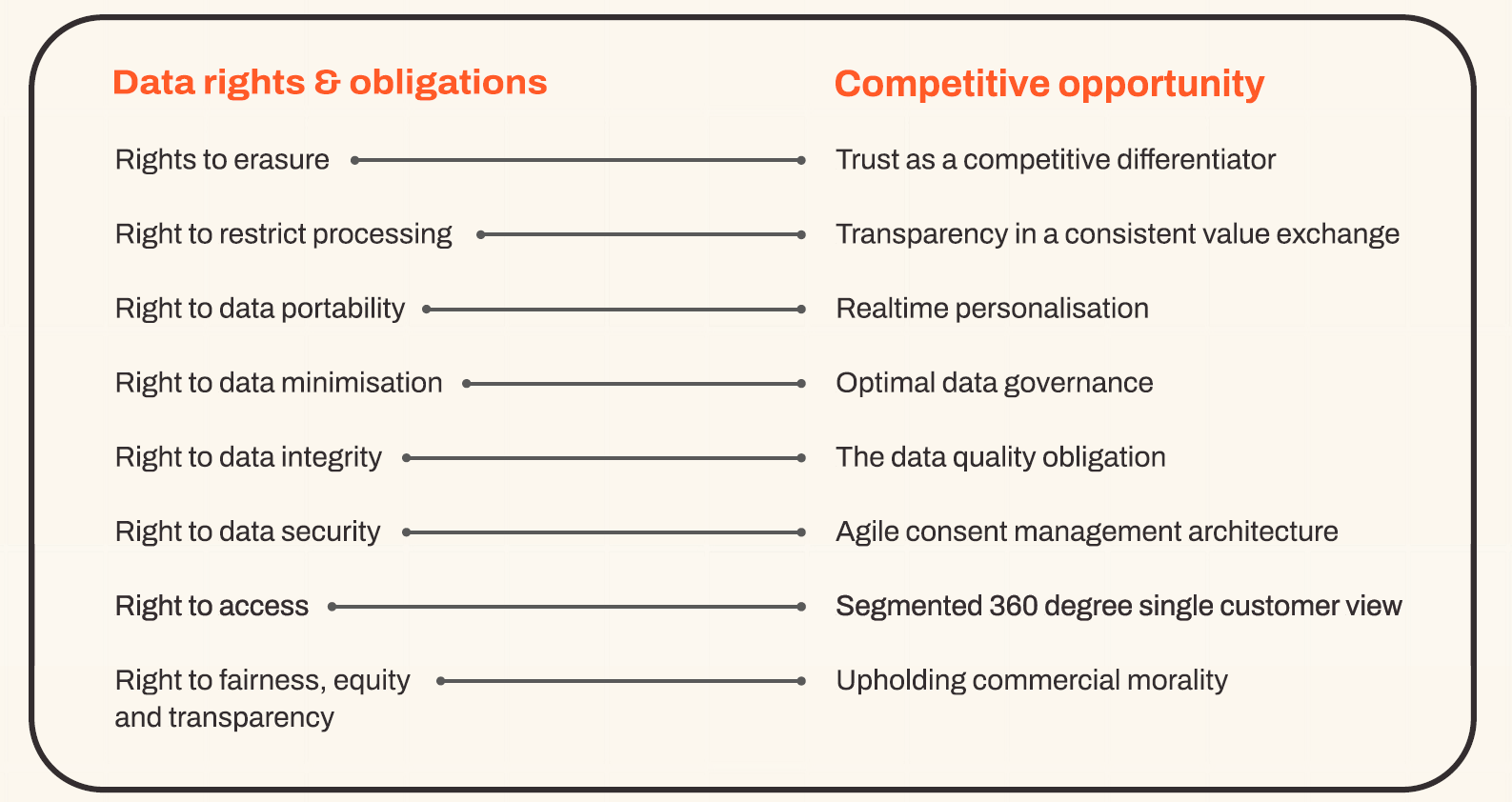
Customer Rights vs Competitive Opportunity
Achieving a competitive advantage through compliance.
Let’s take the “Right to Data Portability and Personalisation” for example. Consumers are entitled to data portability, meaning they can obtain and reuse their personal data across different services. This enables real-time personalisation, offering services that dynamically adapt to current customer needs, enhancing customer satisfaction and loyalty.
We won’t ever have the same amount of data, but if we offer value, trust, and transparency, we can mutually benefit in a privacy first approach to marketing.
Better Privacy = Better for Customers
Through these efforts, we can both be champions of privacy and provide better customer experiences.
- We can address clients’ increasing desire for meaningful, personalised experiences that are 1 to 1
- Have a better offering in a value exchange where consumers feel benefits from sharing data and encourage consented data sharing
- Leverage emerging technologies from this new world to further enhance offerings such as AI
1:1 Customer Experiences
Post-pandemic, customers expect a new benchmark in omnichannel experience, driven by data centralisation and activation in real time.
Data is Consented
Marketers need to have a complete view of the customer journey in order to better understand customer behaviour and preferences.
AI Means More Sales
Customers can surface deals more relevant to them. AI technology allows richer, more detailed and personalised sales pages.
Loyalty and Rewards
Brands with better data can segment customers and use predictive modelling to find offers that resonate.
Privacy Enhancing Technology Landscape
What does the privacy-enhancing technology landscape look like?
These are the foundational technologies online brands are using to have a privacy first approach to marketing.
- Customer Data Platform (CDP)
- Reverse ETL
- Data Clean Room
Customer Data Platform
A Customer Data Platform (CDP) is a software tool that gathers and organises data about customers from various sources. It creates a single, comprehensive profile for each customer, which helps you understand your customers better and tailor marketing efforts to their preferences. In short, CDPs help you improve customer experiences and drive more effective marketing campaigns by centralising and analysing customer data.
Benefits and Challenges
- Centralised data: consolidate customer touchpoints into a single platform
- Personalisation: Advanced segmentation for targeted campaigns
- Privacy and security: Identity resolution and data masking
- Consent management: Ensure data is activated only with user consent
- Implementation challenges: Time-intensive setup, complex ID resolution, potential ‘householding’ issues, CMPs as simpler alternatives
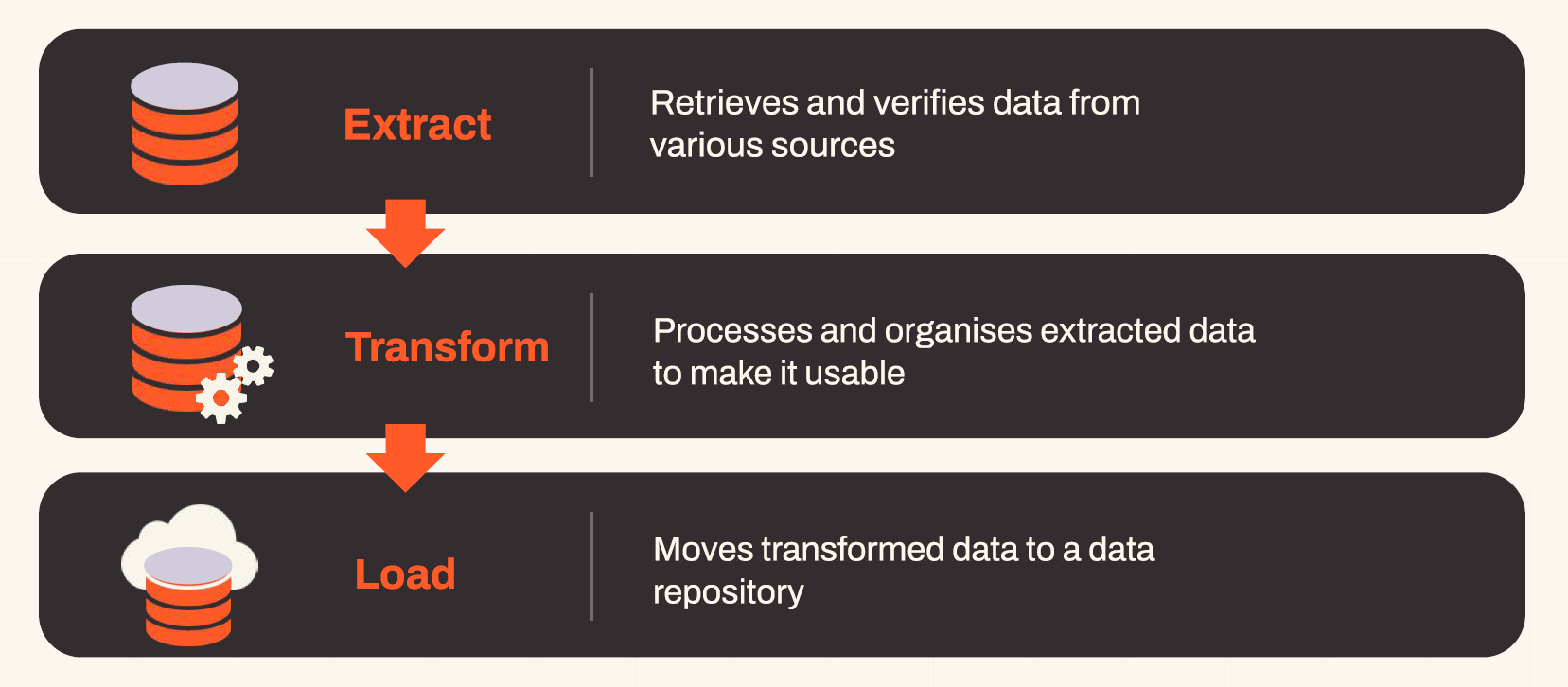
Reverse ETL
Reverse ETL stands for Extract, Transform, Load. It’s a way of managing data, which is important in privacy first marketing. Reverse ETL lets you pull data from your storage when you need it. It has two benefits. First, your data stays in your control, giving you more power. Second, it respects privacy by limiting how much data is shared with outside platforms like Facebook or Google Ads.
Using Reverse ETL with Anonymised Data
- Strategic approach: Secures and focuses on privacy by keeping data within a controlled environment, reducing external data sharing
- Data management redefined: Enables on-demand data extraction from warehouses, optimising data use and integration
- Limits external sharing: Decreases data shared with external platforms, emphasising user privacy
So, do you need a Customer Data Platform (CDP) to use ETL? Not necessarily. CDPs help manage customer data, but using a data cloud platform like Snowflake with an easy ETL tool like Hightouch might work better for you.
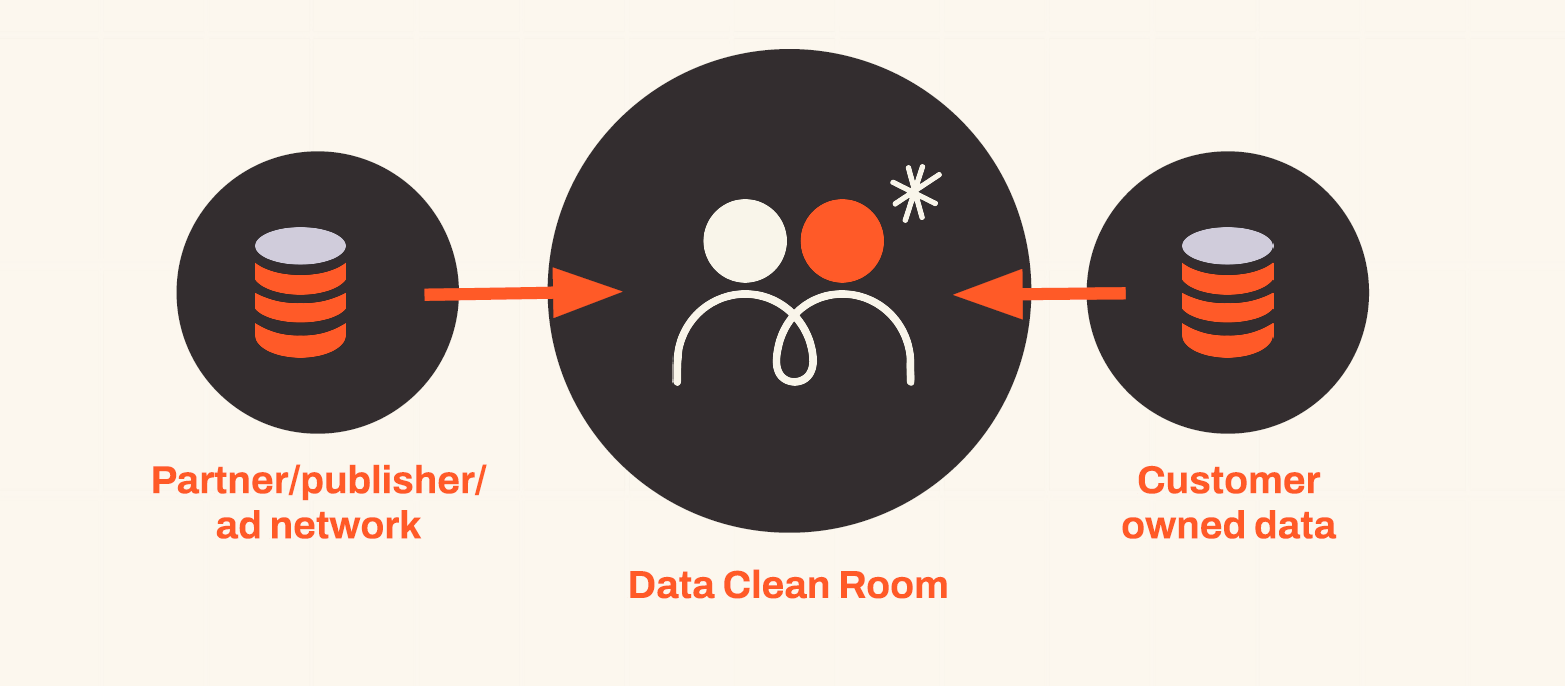
Data Clean Room
A Data Clean Room (DCR) is a secure, neutral environment where multiple data sources can be shared without having to physically exchange the data sets or compromise personal information (PII), IP identifiers or any other form of private data.
A DCR is about providing a complete persistent view of the customer using other first-party data sources without requiring data to be moved into a centralised location, eliminating the risk of exposure and leakage.
Among the highest-profile Data Clean Rooms in the media and advertising world are those run by walled gardens – Google, Amazon and Meta.
- Secure data sharing environment: Facilitates secure, regulated data sharing and analysis between parties while maintaining full control over data usage.
- Privacy and compliance: Offers a solution for accessing crucial data within a regulatory-compliant framework that respects consumer privacy.
- Simplifying complexity: Although not inherently complex, data clean rooms require significant investment and careful consideration in their setup and operation.
- Big tech alternatives: platforms like Google, Facebook and Amazon provide data clean room solutions, yet working with them may present logistical and political challenges.
Minimise the Risk and Maximise the Rewards for Compliance
Complying with global data privacy laws not only aligns with best practices but also offers long-term financial and operational advantages that surpass the initial investment required for businesses.
Core Business Strategies to Implement a Privacy First Approach to Marketing
In the middle of every difficulty lies opportunity.
There are six key components to implementing technology which support data privacy. These overlap with many of the principles of GDPR and The Australian Privacy Principles.
Data Minimisation
Data minimisation means collecting the minimum amount of personal data that you need to deliver an individual element of your service.
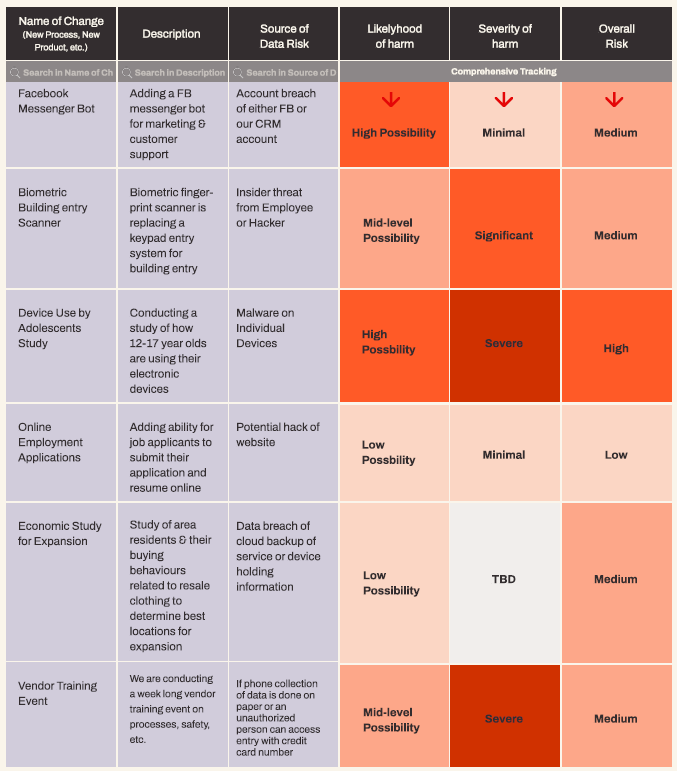
Vendor Risk Assessments
Conduct an in-depth review of data privacy practices, covering breach notifications, privacy notices, data requests, consent, and sharing with fourth parties, ensuring alignment with industry guidelines, frameworks, standards and laws.
Data Protection Officer (DPO)
Ensures that their organisation processes the personal data of its staff, customers, providers or any other individuals (also referred to as data subjects) in compliance with the applicable data protection rules.
Privacy by Design
Data protection in data processing procedures is best adhered to when it’s already integrated in the technology when created.
Training
Data privacy and data privacy awareness training refers to educational courses and programs designed to educate employees about data privacy.
Ethical Data Usage
Respecting fairness, and transparency, as well as the balance between individual rights and societal benefits.
Data Minimisation
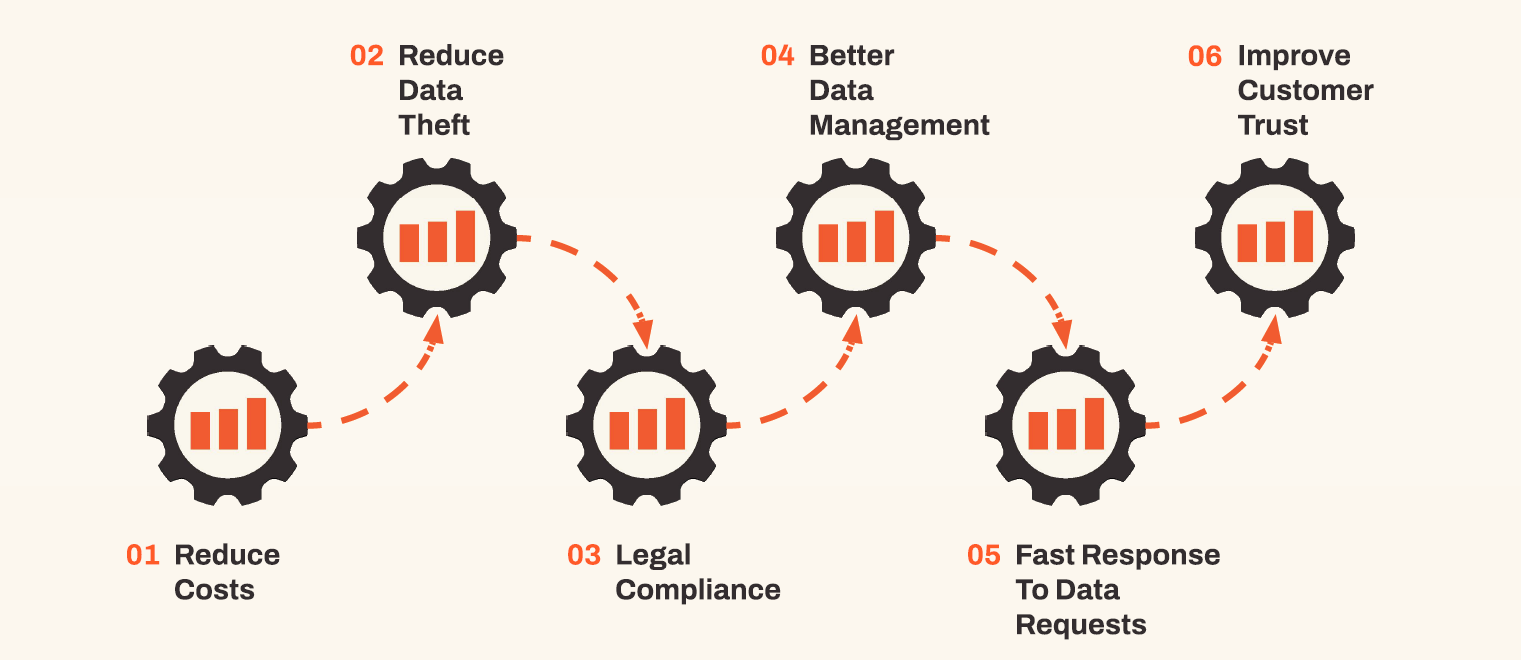
Data minimisation is a principle that states that data collected and processed should not be held or further used unless it is essential for reasons that were clearly stated in advance. Some of the perks of data minimisation are reduced costs, easier to manage data and improved customer trust.
As marketers we often have a tendency to collect data for the sake of collecting data in case we will need it. Less is more. Only collect data that matters.
Why is it important to minimise your data?
Apart from the fact the data minimisation principle is being reviewed and strengthened by the GDPR and there are new obligations for personal data, it also represents best practice with maintaining customer trust and reducing the risk of unauthorised access and other security threats.
How can you practise data minimisation?
When collecting data, remember to ask yourself several questions for each point of data you are planning to collect:
- Does the individual know I am collecting the data?
- How am I planning to use this data?
- Does the individual know why I am collecting the data?
- Is there a way of achieving this purpose without having to collect the data?
- How long will I need the data for to achieve the purpose?
Vendor Risk Assessment
Understand the risk of each of your data and technology vendors
The idea here is to start comparing your different vendors for the use case that you have and ranking them based on different criteria, for example, security practices, the privacy policy support available, etc. Comparing your vendors in this way will help you in selecting the right vendor for the particular need you have. This is a big part of the Privacy by Design policy.
Data Protection Officer
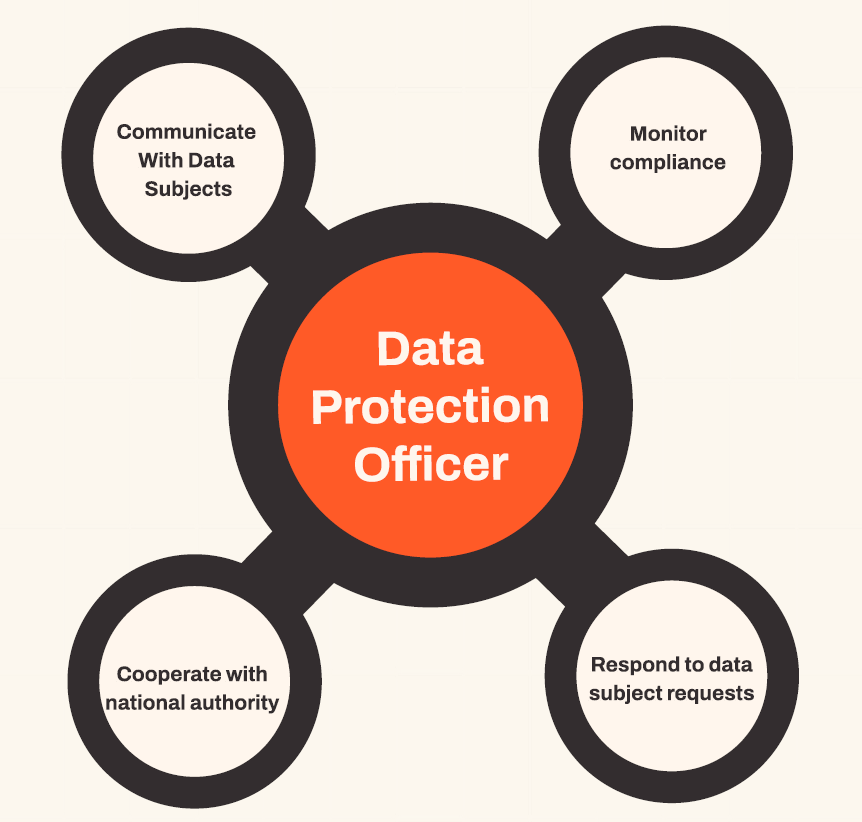
The DPO has an important role to play in a modern and compliant business. A Data Protection Officer (DPO) is a designated individual within an organisation responsible for ensuring compliance with data protection laws and regulations, such as the General Data Protection Regulation (GDPR) in the European Union.
The role of a DPO includes
- Role clarity and compliance: Ensure the organisation understands and complies with data protection laws, working closely with the relevant data protection authority.
- Awareness and education: Inform and educate the marketing team and other relevant stakeholders within the organisation about their data protection rights, obligations, and responsibilities.
- Advice and recommendations: Provide expert guidance on the interpretation and application of data protection rules to ensure marketing strategies are compliant.
- Record keeping: Maintain a comprehensive register of all data processing activities, identifying and mitigating risks associated with specific operations.
- Promote data protection compliance: Assist the organisation in achieving and demonstrating compliance with data protection laws, thereby ensuring accountability.
- Query and complaint management: Address and resolve queries or complaints related to data protection, either initiated by internal requests or independently.
- Cooperation with data protection authorities: Facilitate effective communication and cooperation with the data protection authority, responding to investigations, inspections and other regulatory actions.
- Monitoring and reporting non-compliance: Proactively identify and report any instances of non-compliance with data protection rules to the organisation, advising on corrective actions.
Privacy by Design
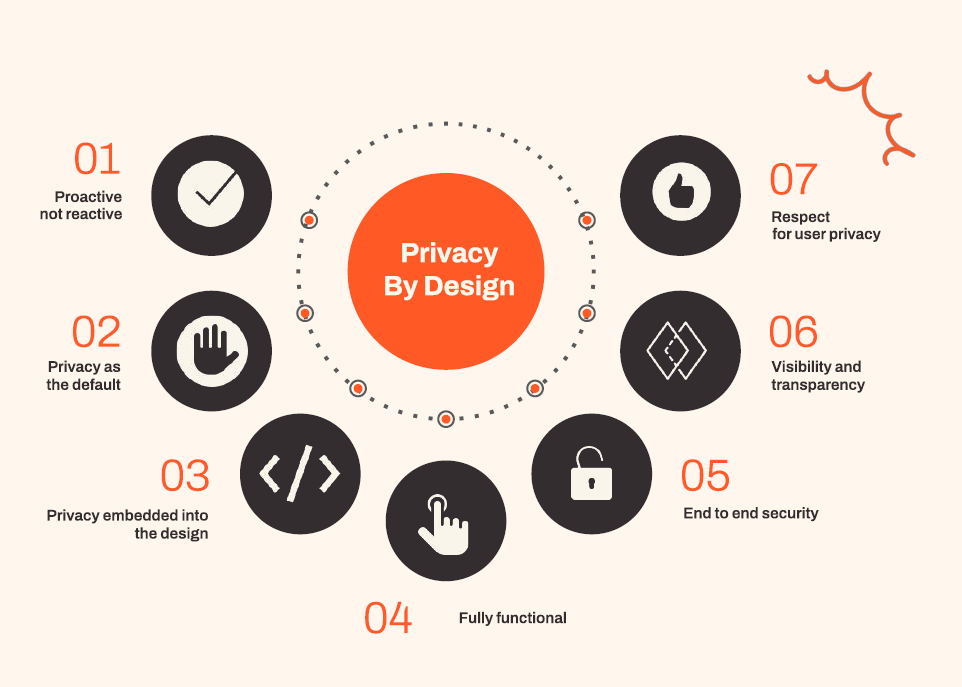
Privacy by Design (PbD) is a new way of thinking about privacy in a digital world. It was thought up by Dr. Ann Cavoukian in the 1990s. It concludes that privacy should be a key part of designing products and systems from the start. It has seven main ideas, including protecting privacy from the beginning, making privacy the default setting, and having security all the way through.
Privacy by Design makes sure that privacy is built into the process from the start, not just added on at the end.
The General Data Protection Regulation (GDPR) in the European Union has made Privacy by Design a legal requirement for organisations that handle personal data. This shows how important privacy is around the world. PbD principles are now key guidelines for companies everywhere as they try to respect and protect personal privacy in their work and interactions.
Proactive, not reactive; preventative, not remedial
Adopting a forward-thinking approach to privacy, anticipating and preventing privacy issues before they occur, rather than addressing them after the fact.
Privacy as the default setting
Ensuring that privacy settings are automatically set to the highest level of privacy by default, requiring no additional action from the user to protect their privacy.
Privacy embedded into design
Integrating privacy into the architecture of IT systems and business practices from the outset, making it an integral part of the product development process.
Full functionality – positive-sum, not zero-sum
Designing systems that enhance privacy without sacrificing functionality, moving away from the mindset that trade-offs between privacy and security are inevitable.
End-to-end security – full lifecycle protection
Implementing comprehensive security measures that persist throughout the entire lifecycle of the data, ensuring that personal information is securely managed from collection to deletion.
Visibility and transparency – keep it open
Maintaining transparency with users about how their data is used, processed, and protected, offering clear, user-friendly options to control their personal information.
Respect for user privacy – keep it user-centric
Prioritising user privacy preferences and needs, ensuring users retain control over their personal information and are treated with respect throughout their interactions with the service or product.
Build a Best Practice Privacy First Marketing Technology Stack
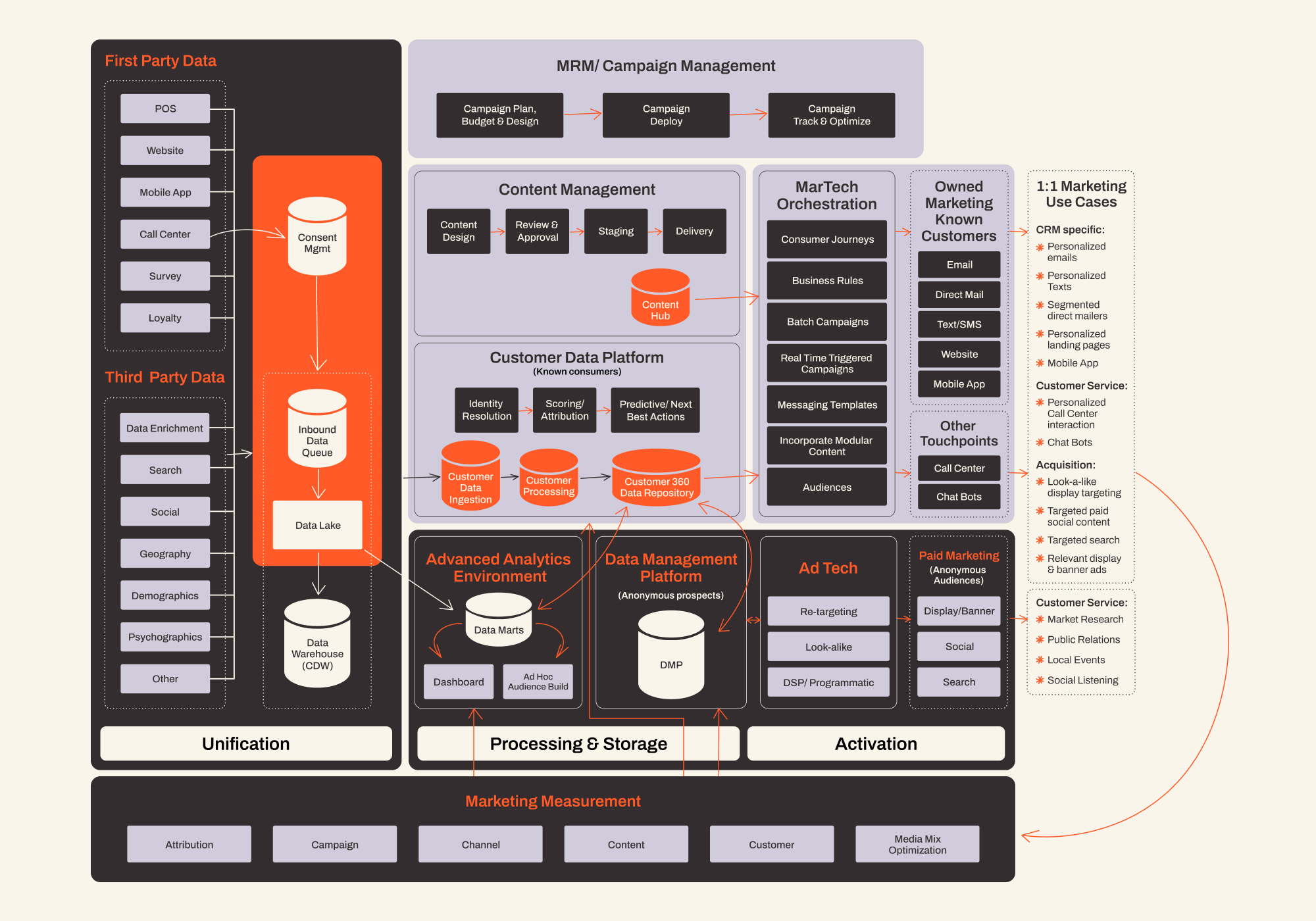
An approach to build a best practice and privacy first marketing technology stack, to measure and activate customer data. A best practice privacy first martech stack can be visualised at a high level in quadrants supported by a backbone.
Backbone
Secure data infrastructure
Establish a secure and compliant data infrastructure that serves as the foundation for all marketing activities, prioritising data privacy and security.
Discover
Insightful data analysis
Implementing tools and processes for analysing data within privacy guidelines, focusing on deriving insights from aggregated and anonymised data sets.
Decide
Privacy compliant communication
Ensure that all marketing communications adhere to privacy regulations, using consent-based and privacy-aware channels to reach customers.
Activate
Engaging with consent
Activate marketing strategies based on explicit consumer consent, leveraging zero-party and first-party data to personalise experiences without compromising privacy.
Automate
Efficient and ethical use of AI
Utilise artificial intelligence and machine learning in an ethical manner, automating tasks for efficiency while ensuring transparency and control for consumers.
Privacy First Martech Stack
Using the privacy first martech framework can turn problems into chances for winning. It focuses on five key areas:
- A safe main structure
- Smart discover
- Delivery that follows rules
- Activation based on agreement, and;
- Fair automation
A privacy first martech stack helps businesses follow a privacy first approach to marketing. This method makes sure rules are followed and also helps earn customers’ trust. This leads to a future in marketing that is more long-lasting and focuses more on customers.
Let’s take a look at our best practice privacy first application. Our stack contains 4 pillars:
- Unification: Our inputs and data collection
- Processing & Storage: How we securely hold and augment our data
- Activation: Our outputs or delivery to our consumers
- Marketing Measurement: This underpins everything
While these 4 are key, they connect to other elements of the tech stack, including:
- Customer Data Platforms: Centralised command centre, aggregating data from various sources including our existing customers
- Content Hubs: Library which comprises our messaging
- Martech Orchestration: Brings together multiple components or instruments in harmony to create a unified and cohesive marketing strategy
Underlying these sections is a strong emphasis on data minimisation, anonymisation, encryption, and transparency to ensure that user privacy is prioritised throughout the marketing process. Additionally, regular audits and compliance checks are essential to maintain alignment with evolving privacy regulations and industry best practices.
Let’s look at the practical application of our marketing tech stack model, a model that’s been successfully implemented across many of our clients. Let’s break it down into four key sections: Discover, Activation, Decision and Automation.
Discover
Data Discovery encompasses a wide range of human-driven functions, from predictive modelling to digital analytics.
Questions
- What is the retention period of all data?
- What is the need for personally identifiable information (PII) in all systems?
Activation
Activation is where we turn insights into action, engaging our audience through targeted, privacy first strategies.
Decision
(Information) Delivery refers to decision-making, the ultimate brain-powered task.
Questions
- What does insight management look like? KPIs? Cross-channel campaign management? ROI formula?
Automation
Automation involves systematising and automating multiple tasks, many of which fall within the realm of AdTech.
Questions
- How can we trust that the systems will perform as expected?
- Where is the risk PII is exposed?
Our marketing tech stack model is designed to enhance our marketing efforts through Discovery, Activation, Decision, and Automation, all while being mindful of privacy and compliance. By addressing critical questions at each stage, we can navigate the complexities of modern marketing.
The data privacy landscape is rapidly evolving. There are big benefits to proactively addressing it and big consequences from ignoring it. Data privacy will continue to evolve in favour of the consumer. Compliance is not a choice. As an online brand is makes sense to have a privacy first approach to marketing.
Measurement is being limited and cookie consent is just the start. We need to ask for user consent before collecting data. The first thing you need to do now is to designate a Data Protection Officer to help you navigate the changes. CDP, Reverse ETL and Data Clean Rooms are technologies you should start exploring and in terms of applying a privacy first approach to your strategy, apply Privacy by Design.
Need help?
In data we trust, and that data has to be safeguarded properly. We help you define your data governance by building a collection of processes, templates and frameworks for your team to use.
We also offer practical training to support data governance best practices while following expectations set by policies and standards.
Need help managing and securing your data? Talk to us today.